Learn how to safeguard your personal information and prevent
identity theft with these safety tips.
If you are worried about hackers stealing your personal information, you’re not alone—and you’re not crazy. A study by McMaster University found that 1.7 million Canadians were victims of identity theft in 2008, and the cost of identity theft has been estimated at
$1.9 billion annually.[1] Once hackers gain access to people’s names, Social Insurance Numbers and other personal information, the victims are at risk for
identity theft, credit fraud and even financial ruin.
Major retailers, insurance companies and the federal government have all been hit by cyber attacks; it’s not just big business and government agencies that hackers are after. Any organization or individual who collects and stores personal information—from mom-and-pop
shops to the PTA website—is vulnerable to cyber crime.
Protecting yourself, your loved ones and your assets might seem like an overwhelming task, but there are some simple steps you can—and should—take to protect yourself. Follow these cyber crime-stopper tips to keep your personal information safe and sound.
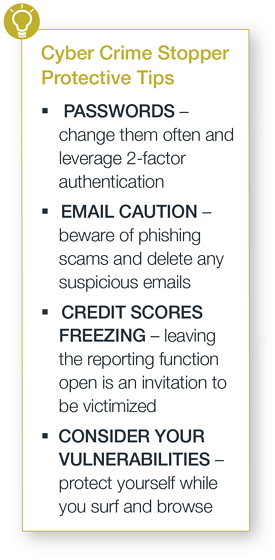 TIP I: Be
smart about passwords
TIP I: Be
smart about passwords
While it is ideal to change
passwordsoften and turn on two-factor authentication on every possible site, chances are you’re not doing it.
The best way to manage passwords is to employ a password management program that produces complex passwords, stores them in the cloud and allows you to invoke your passwords even from a compromised system.
These programs typically depend on a master password. It is important to know what makes a good one -- the real secret to a successful password is its length. Use a long pass phrase as the master key to your password manager. The longer the better, especially if
larded with symbols that would not appear in any existing piece of literature. Hence, go22fly22a2222kite! is better than go fly a kite.
TIP II: Be
cautious with email
Many cyber attacks are traced to
“phishing” scams. These fraudulent emails appear to come from legitimate companies, local businesses, friends and volunteer organizations and direct people to a website that either asks for personal information or—when clicked upon—infects the user’s computer with malware. You can prevent a phishing
attack by being suspicious of emails that contain:
- grammar or spelling mistakes
- generic salutations, requests
- requests for personal, healthcare or credit card information
- suspicious attachments
- suspicious links
If you are suspicious of an email, call the sender to verify that the email is legitimate. And if an email seems suspicious or too good to be true, feel free to hit the delete button.
TIP III: Freeze
your credit scores
Freezing your credit score with the three credit-reporting agencies makes it more difficult for identity thieves to open new accounts in your name. That’s because most creditors need to see your credit report before they approve a new account. If you want to open a new account, rent an
apartment or buy insurance, you can lift the freeze temporarily (either for a set amount of time or for a specific creditor) by contacting the credit-reporting agencies.
Because people do not apply that often for credit or housing, leaving the reporting-function open is an invitation to be victimized. Contact the three credit reporting agencies to freeze your credit:
Equifax
Experian
Transunion
TIP
IV: Watch for
hidden vulnerabilities
A few extra steps can help protect you while you surf and browse at home.
- Turn on ‘encryption’ on all computers. Both Mac and Windows have system options that encrypt the hard drive. As a result, data cannot be compromised easily if the laptop or computer is stolen.
- Keep your operating system, browser, anti-virus and other critical software up to date.
- Be cautious with online banking. You may even consider dedicating one computer or device just to banking and tax activity, with no other Internet browsing or activity, to limit risk of infection.
Ultimately, there are no guarantees. But experts affirm that when hackers run up against secure information, they are more likely to move on to an easier target.
[1] “Canada’s Cyber Security Strategy.” Public Safety Canada, 2010.